
New research from Microsoft’s Threat Intelligence team exposed the activities of a threat actor named DEV-1101, which started advertising for an open-source phishing kit to deploy an adversary-in-the-middle campaign.
According to Microsoft, the threat actor described the kit as a phishing application with “reverse-proxy capabilities, automated setup, detection evasion through an antibot database, management of phishing activity through Telegram bots, and a wide range of ready-made phishing pages mimicking services such as Microsoft Office or Outlook.”
SEE: Phishing attacks: A guide for IT pros (free PDF) (TechRepublic)
Microsoft uses DEV followed by a number as a temporary name for an unknown, emerging or developing cluster of threat activity. After there is enough data and high confidence about the origin or identity of the threat actor, it is given a real threat actor name.
Jump to:
- What is an adversary-in-the-middle phishing attack?
- How these phishing kits are used
- Potential impact of this phishing kit
- Rising price of the phishing kit
- How to protect from this AitM threat
What is an adversary-in-the-middle phishing attack?
In an adversary-in-the-middle phishing attack, a bad actor intercepts and modifies communications between two parties, typically a user and a website or service, to steal sensitive or financial information, such as login credentials and credit card data.
An AitM campaign is more difficult to detect than other types of phishing attacks because it doesn’t rely on a spoofed email or website.
How these phishing kits are used
The phishing kits have been used with several approaches.
One approach, explained by the researchers, is what was used by DEV-0928, another threat actor tracked by Microsoft. DEV-0928 starts the attack by sending an email to the target (Figure A).
Figure A
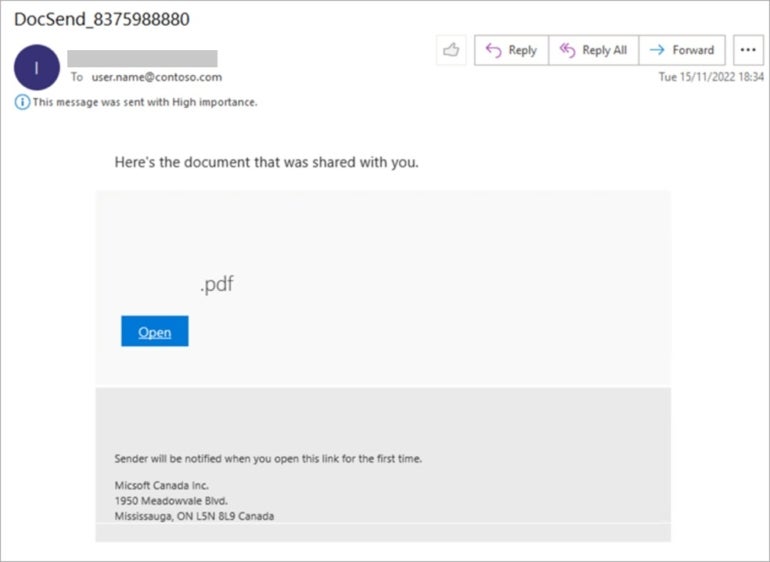
When the user clicks the Open button, the antibot functionalities of the phishing kit come into action. If a bot is detected, the phishing kit might provide a redirection to any benign page configured by the attacker — the default one is example.com.
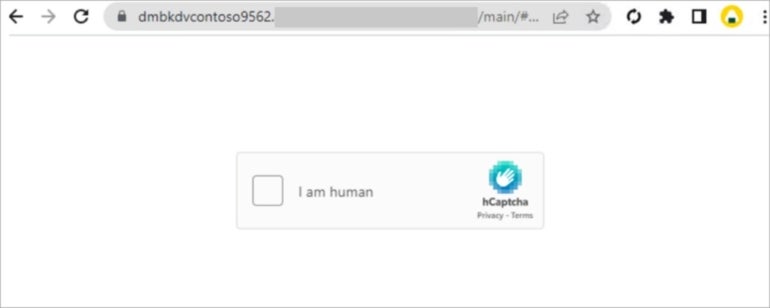
Another technique might be to launch a CAPTCHA request to evade detection and ensure a real user is behind the click (Figure B).
Figure B
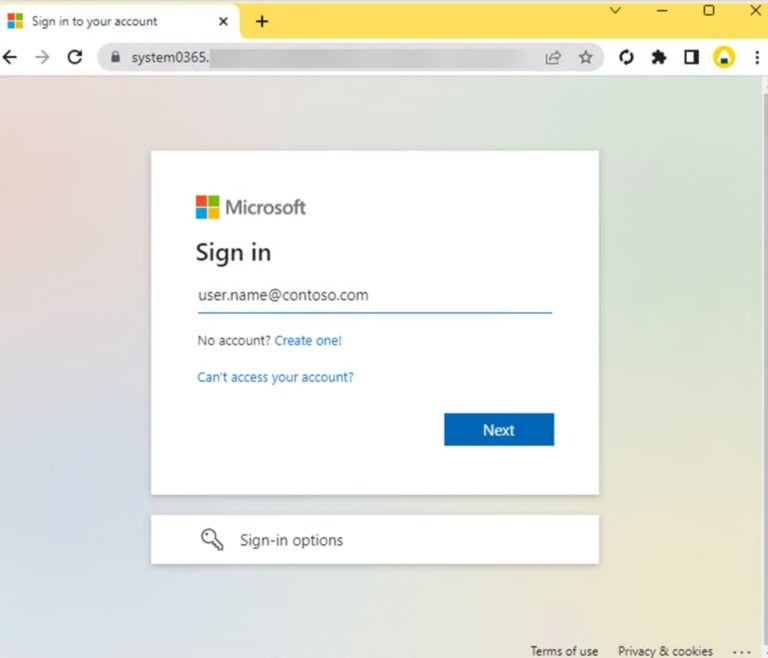
The user is shown a phishing page hosted by an actor-controlled server (Figure C).
Figure C
How AiTM campaigns bypass multi-factor authentication
If the user has provided the phishing page with their credentials and enabled multi-factor authentication to log in to their real account, the phishing kit stays in function to activate its MFA bypass capabilities. The phishing kit acts as a proxy between the user and the legitimate service.
The phishing kit logs in to the legitimate service using the stolen credentials, then forwards the MFA request to the user, who provides it. The phishing kit proxies that information to the legitimate website, which returns a session cookie that can be used by the attacker to access the legitimate service as the user.
Potential impact of this phishing kit
Microsoft has observed millions of phishing emails sent every day by attackers using this kit, but its diffusion might be even larger. In fact, any attacker might subscribe to the phishing kit license and start using it. While email is probably the most common method of reaching victims, attackers might also deploy it via instant messaging, social networks or any channel they might target.
Rising price of the phishing kit
The threat actor started selling the kit on a cybercrime forum and on a Telegram channel around June 2022 and announced a price of $100 USD for a monthly licensing fee. Due to the increase of attackers interested in the service, the price reached $300 USD in December 2022, with a VIP license offer for $1,000 USD.
How to protect from this AitM threat
- Always deploy and maintain MFA when possible: While techniques such as the adversary-in-the-middle still allow bypassing MFA, it is a good measure that makes it more complex to steal access to user accounts or services.
- Enable conditional access and Azure AD security defaults: Microsoft recommends using security defaults in Azure AD as a baseline set of policies and enabling conditional access policies, which allow the evaluation of sign-in requests based on several factors such as the IP location information, the device status and more.
- Deploy security solutions on the network: This will help detect phishing emails on email servers as well as any malware or fraud attempt on all the other parts of the network.
- Keep software and operating systems up to date: Keeping software up-to-date and patched will help to avoid falling for common vulnerabilities. To help with this step, consider downloading this patch management policy from TechRepublic Premium.
- Educate users about computer security and cybercrime: Provide employee training with a focus on phishing, as it is the most common way to target users with malware and fraud. To help with this step, consider downloading this security awareness and training policy from TechRepublic Premium.
Read next: For credentials, these are the new Seven Commandments for zero trust (TechRepublic)
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.







