DevSecOps: AI is reshaping developer roles, but it’s not all smooth sailing
A report by GitLab finds that AI and ML in software development workflows show promise, but challenges like toolchain complexity and security concerns persist.
PURPOSE Every enterprise needs to establish a plan of action to assess and then recover from unauthorized access to its network. This policy from TechRepublic Premium provides a foundation from which to start building your specific procedures. From the policy: ASSIGN AN INCIDENT RESPONSE TEAM An incident response team should be put together and a ...
PURPOSE Every department, regardless of size, needs to employ and account for depreciation — particularly if that department manages assets such as laptops, servers, and production machinery. How else are you going to know when it’s time to purchase new equipment? With the help of this worksheet from TechRepublic Premium, you’ll be able to calculate ...
PURPOSE Collaboration tools exist within a wide range of services, from voice calls to version control systems and everything in between. But for average enterprise businesses, the tools that make work-life exponentially easier are the basics: Voice. Video. Screen sharing. LDAP integration. Web and mobile apps. Third-party integration. Your business might be able to get ...
PURPOSE Some of the most important tools in business are used for collaboration. Without these types of solutions, your staff would struggle to remain as productive as needed. TechRepublic Premium dug into some of the top collaboration tools on the market as a comparison to help you know which offers the tools you need and ...
Looking for the right password management fit for your organization? These eight options all have something to offer, and one may be the best fit for you.
Find the best applicant tracking system for your business needs in 2023 with our comprehensive guide. We review the top 10 ATS solutions to help you make the best decision.
Antivirus software protects your data against cybercriminals, ransomware and malware. Compare the best software now.
VPNs are an essential component in small and medium-sized businesses' cybersecurity toolkit. Here's how leading VPN services for SMBs compare.

A new phishing campaign abuses OneNote documents to infect computers with the infamous AsyncRAT malware, targeting users in the U.K., U.S. and Canada.

Enjoy your music on-the-go without isolating your surroundings using the Mu6 Ring Open-Air Bluetooth Headphones — on sale for just $55.

Determining how and when to renew support contracts can be tedious and time-consuming. Our vendor contract renewal planner will help you schedule support renewals and budget the related costs. From the planner: Some companies schedule their support contract renewals to take effect all at once, such as on January 1. This provides a convenient renewal ...

Without appropriate access management controls, businesses are at significant risk from the loss or theft of both physical and digital assets. Access management controls establish who is allowed the appropriate level of access in order to do their jobs, while reducing the potential for damage or harm to the company. The purpose of this policy ...

Discover how to take care of your company servers with the Linux/UNIX Certification Training Bundle — now on sale for 97% off!

Veritas, the multicloud company, has been selected by the United States Postal Service for new data modernization and regulatory compliance efforts. Get the details here.

The proposed project uses a hydrogen-powered autonomous airplane. BT Group seeks to improve connectivity and enhance or replace traditional cell masts.

Faster speeds and greater connectivity herald next-generation mobile. However, some improvements are still science fiction.
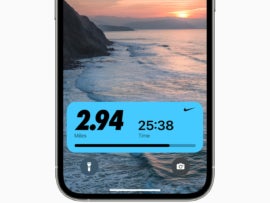
Live Activities are a new app-based tile that can appear on the Lock Screen in iOS 16 and keep you up to date with information. Learn how to use them and how to enable frequent updates.

If you're looking for a graph database to use for your next project, Neo4j is an open-source option that can encode and query very complex relationships.